Ransomware Recovery
We'll get you back online without skipping a beat.

Ransomware is a Threat to Consider
Most businesses don't consider ransomware defense until after they're been compromised. If you've found yourself under the mercy of Ransomware set by an intruder, we can help.

Have I Been Compromised?
If you're unsure if you've been compromised or not, take a look at a few examples below:
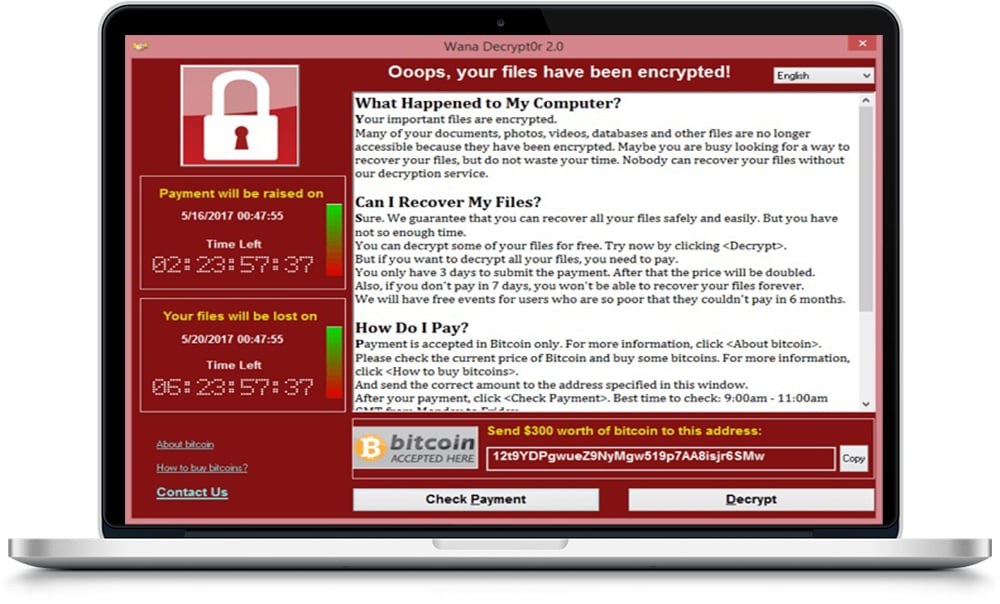
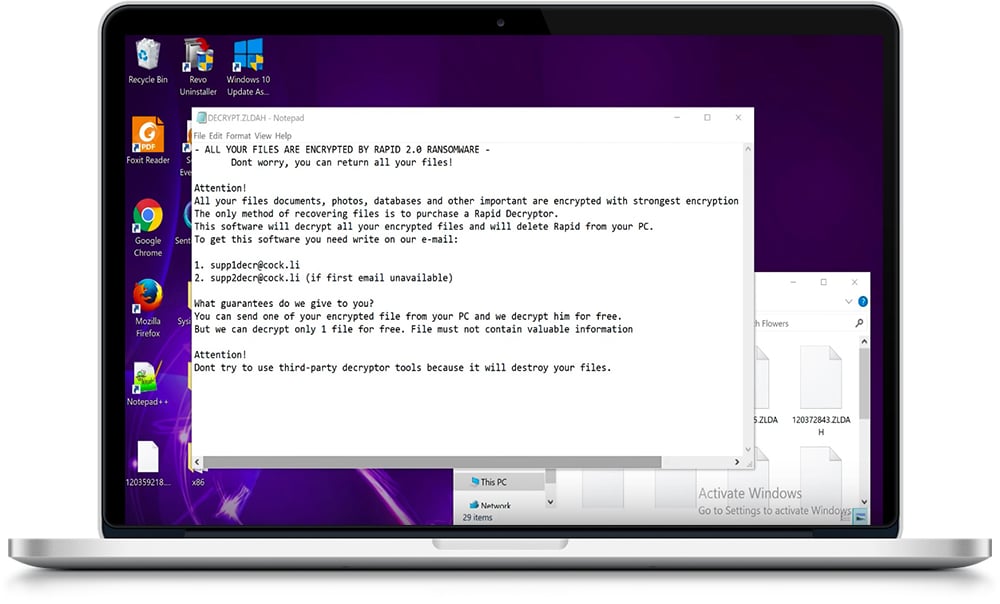
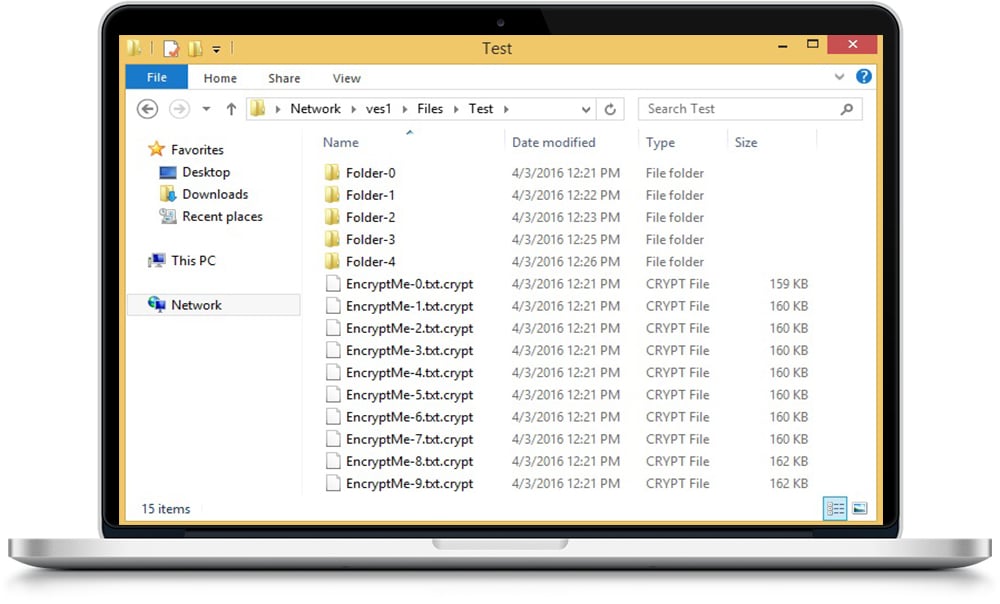
Down the Path to Recovery
After a compromise, getting your systems back up and running can be a difficult task. You need to know what information has been compromised, which systems don't work, and if any of your client's data has been compromised as well. We can handle the entire recovery process from start to finish.
Prevent Further Encryption
We deploy security measures and protocols to prevent the ransomware from spreading to other systems and devices.

Identifying the Compromise
We scan your systems from top to bottom to get a full view of what has been compromised.

Backup and Recovery
Once we receive approval, we begin the process of restoring from backups or recovering the data that we're able to decrypt.

After Action Report
Once we complete our recovery, we'll provide you with the data we could recover, and where the intrusion came from.

If you've been hit, we can help.
Give us a call, we'll get you back up and running.

